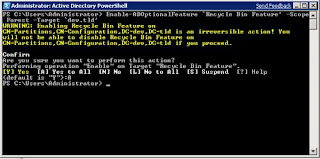
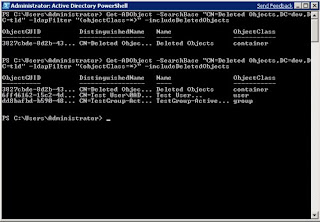
There are a number of new
Active Directory Domain Services features in Windows Server 2008. These new features improve auditing, security, and the management of Active Directory Domain Services and show Microsoft's commitment to evolving Active Directory Domain Services. The following is an overview of the new Active Directory Domain Services features that are in Windows Server 2008.
AuditingWindows Server 2008 introduces significant changes to Active Directory Domain Services auditing. Active Directory Domain Services auditing in Windows Server 2008 is more granular than previous versions and provides you with more control over what is audited.
Active Directory Domain Services auditing is now divided into the following four subcategories:
* Directory Service Access
* Directory Service Changes
* Directory Service Replication
* Detailed Directory Service Replication
You can disable or enable
Active Directory Services auditing at the subcategory level. For each subcategory, you can also configure whether to log successful events, failed events, both successful and failed events, or no auditing.
In Windows Server 2008, the new Directory Service Changes subcategory allows you to log the old value and new value of a changed attribute, in addition to the attribute name.
Windows Server 2008 also provides the ability to exclude the logging of changes to specific attributes by modifying the attribute properties.
The Active Directory Domain Services auditing subcategories are viewed and configured by using the Auditpol.exe command-line tool.
Fine-Grained Password Policies
Windows Server 2008 introduces the ability to create multiple password policies in a single domain, which is another first for
Active Directory Domain Services. The introduction of fine-grained password policies in Windows Server 2008 allows organizations to create and manage multiple password policies and account lockout policies to meet diverse security requirements.
You can configure the same password policy and account lockout settings in a fine-grained password policy as you can at the domain level. Fine-grained password policies can be linked to users and to global groups. Because users can inherit multiple password fine-grained password policies, a precedence setting has been included to allow you more granular control.
Fine-grained password policies are configured by using the ADSI Edit snap-in.
Read-Only Domain Controllers
Another first for Active Directory Domain Services is the introduction of a new type of domain controller in Windows Server 2008, the read-only domain controller (RODC). RODCs are intended to assist you in situations in which domain controllers must be deployed in locations where physical security cannot be guaranteed, such as branch offices.
Microsoft has implemented a number of mitigating measures to ensure a compromised RODC does not impact the rest of your Active Directory Domain Services environment. These measures include the following:
* Read-only database
* Unidirectional replication
* Credential caching
* Administrator role separation
* Read-only Domain Name System (DNS)
Restartable Active Directory Domain ServicesWindows Server 2008 now includes a true service, which allows you to stop, start, and restart Active Directory Domain Services without having to restart the operating system.
In Windows 2000 Server and
Windows Server 2003, the operating system on a domain controller had to be restarted in Directory Services Restore Mode for most maintenance and recovery. However, Windows Server 2008 now provides the ability to start, stop, and restart the Domain Controller service.
The domain controller service can be manipulated by using the Services snap-in or the Computer Management snap-in.
Database Mounting ToolWindows Server 2008 includes a new ability to take snapshots of an Active Directory Domain Services database and mount these snapshots into a new database mounting tool.
The database mounting tool allows you to view an
Active Directory Domain Services object's previous state. You can then use this to compare the object's previous state to the object in production. This is particularly useful if you know that an object's attributes were changed, but do not know what the previous value of the attributes were.
User Interface ImprovementsA number of user interface improvements have been made in Windows Server 2008. The following is a list of some of the most noteworthy interface changes in Windows Server 2008:
* New installation options for domain controllers.
* A more streamlined and simplified installation process.
* Improvements to the Active Directory Users and Computers console.
* A built-in Attribute Editor, which is accessible on the properties page of each object in the Active Directory Domain Services management tools.
Owner RightsWindows Server 2008 now provides the ability to limit the default permissions that the owner of an object is given. In previous versions of Windows, the owner of an object was given the ability to read and change permissions on the object, which was more than they required in most cases. This new functionality in Windows Server 2008 also applies to Active Directory Domain Services objects.
Source:
http://www.enterpriseitplanet.com/networking/features/article.php/3796561