Tuesday, December 30, 2008
Managing Groups: Exchange and Active Directory Admins Sound Off
Imanami also discovered that in the organizations surveyed, two percent of the people still in Active Directory are no longer employed by the company, or 60 people in an organization of 3,000 users. Imanami surveyed IT pros involved in managing groups and other aspects of Microsoft Exchange management in organizations with at least 1,000 email users.
Based on responses, Imanami calculated that for every 1,000 users, some lucky IT pro spends about six hours per week managing groups in AD. Assuming an organization hires an IT pro at $90,000 a year and his or her job includes this task, Imanami calculates it costs $13,050 per year to manage groups in Active Directory.
“We know how much our solution costs—what surprised us was how much they're paying: one employee for every 5,000 users,” says Edward Killeen, Imanami’s director of sales and marketing. “At up to 250 employees, it's okay to manage groups manually. We usually find at 250 employees the pain starts---there are a lot of groups. Why not automate it and be done with it?”
“People aren’t aware of a solution,” Killeen says. “The good news is that you don’t have to buy ILM. ILM comes with its own nomenclature. Most product suites are ‘Frankenproducts,’ made from acquired products put together. We’re purpose built. Our customers appreciate that they can deploy this without hiring someone.”
Imanami’s conclusions, among other things are that "Group management is not the most serious problem faced by Exchange managers, but it is a serious one that presents a number of security problems.” To compare your experience to those of the IT pros surveyed, visit Imanami’s website.
Source: windowsitpro.com/article/articleid/101004/managing-groups-exchange-and-active-directory-admins-sound-off.html
Monday, December 22, 2008
Disable the Password for a User in Windows Server 2003 Active Directory domain
The default password filter (Passfilt.dll) included with Windows Server 2003 requires that a password:
Is not based on the user’s account name.
Contains at least six characters.
Contains characters from three of the following four categories:
Uppercase alphabet characters (A–Z)
Lowercase alphabet characters (a–z)
Arabic numerals (0–9)
Nonalphanumeric characters (for example, !$#,%)
Security Warning: Bare in mind that this setting can only be enabled/disabled at the domain level, and NOT on an OU level. Disabling the password requirement for an entire domain will lower your security configuration, and should only be done when absolutely necessary.
In order to disable this requirement you need to edit the Default Domain Policy for your domain.
1. Go to Administrative tools folder.
2. Double-click on the Default Domain Security Policy icon.
3. Note: If for any reason you don't see that icon you can still edit the Default Domain Group Policy from the AD Users and Computers snap-in, or from a GPMC window.
4. Navigate to Security Settings > Account Policies > Password Policy.
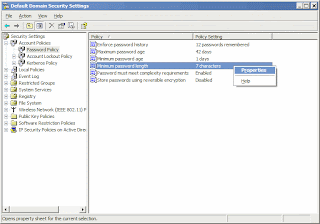
5. Right-click on the Minimum Password Length option in the right pane and select Properties.
6. Keep the V on the Define Setting selected! Do not remove the V from that check-box. Removing the V will cause the GPO to revert to the default setting, which is what we are trying to remove in the first place.
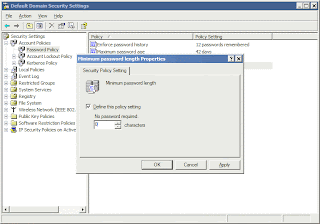
7. Enter 0 (zero) for the number of minimum characters required in a password.
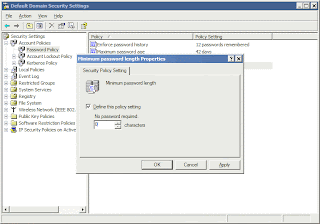
8. Now double-click on the Passwords Must Meet Complexity Requirements option in the right pane.
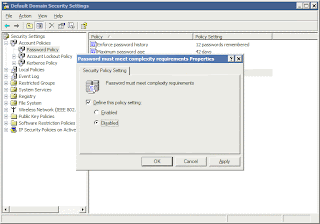
Again, do not remove the V from that check-box. Instead, select Disabled.
9. Click OK all the way out and close the GPO window.
Source: petri.co.il/disable_password_requirement_in_win2003_domain.htm
Monday, December 15, 2008
NET's UC Gateways AddingIntegration Capabilities to MS Active Directory
VoIP technologies innovator Network Equipment Technologies gave its unified communications platform a boost today by adding integration capabilities of Microsoft Active Directory (AD) and other Lightweight Directory Access Protocol solutions to its VX Series gateways.
The directory integration is designed to provide migration benefits to a converged data/voice infrastructure, such as Microsoft Office Communications Server 2007.
While the benefits of the upgrades are many, its primary function is to allow customers to leverage the directory integration features of the VX Series UC Gateway. By using information from AD, customers now have the ability to add enterprise mobility applications to the UC solution.
The applications include the use of AD or LDAP as a single point-of-administration, which is important for allowing customers to perform all moves, adds and changes in one place, according to Talbot Harty, chief development officer at NET.
"The ability to use AD to drive voice and fax functions in a converged environment saves administrators and end-users significant time and effort, while also enabling companies to implement all kinds of useful call management rules," said Harty.
In addition, the ability to flexibly define call-routing rules using AD or LDAP fields has an important function for administrators. This simplification of phased technology migrations – through identification which end-users are served by Microsoft OCS, the PBX,Cisco Manager – has significant business value, according to Harty.
"By delivering robust AD and LDAP integration in our VX Series UC Gateways, we provide customers migrating to Microsoft OCS and other UC solutions.”
NET Quintum, the wholly owned subsidiary of NET, has increased its footprint in recent months within the OCS Server 2007 community. The company has developed VoIP solutions that allow OCS 2007 to be connected to the PSTN, allowing for voice communications outside the IP network. NET Quintum Tenors make it easier to connect Microsoft Office Communications Server 2007 with a Microsoft specific configuration wizard and a wide variety of product options.
The VX Series UC Gateway's AD and LDAP support also provides advantages to resellers and integrators making it easier to install, configure and maintain convergence solutions, according to Jeff Zaremba, senior director of Collaboration Technologies at Avanade.
"Directory integration provides real value to customers by providing a consistent method for managing call routing based on Active Directory when implementing unified communications solutions such as Microsoft Office Communications Server 2007," said Zaremba. Avanade was founded in 2000 byAccenture and Microsoft Corporation.
"Additionally, it provides flexibility in migration by allowing customers to migrate over time as their business requirements dictate. For Avanade, directory integration enables us to implement more sophisticated solutions for our customers with less time, effort, and technical complexity."
More information about the VX Series UC Gateways and the application of directory integration is available at VX Gateways and Active Directory.
Source: http://unified-communications.tmcnet.com/topics/enterprise-voip/articles/47298-nets-uc-gateways-provide-integration-with-ms-active.htm
Friday, December 5, 2008
Microsoft's new hosted services: What are your options?
Whether today's announcement of Microsoft-branded hosted services actually adds up to a savings for a business customer, depends on how that customer is getting or has gotten its software. Right now, the Exchange Online service can host mailboxes for as little as $10 per month per client, with a five-user minimum. That's about the industry average; other firms presently offer Exchange hosting for between $8 and $15 per month.
But Microsoft's not entering this market to simply lend its voice to the ongoing chorus. On an a la carte basis, it's also offering SharePoint Online hosting for managing a collaborative document sharing site (at $7.25 / user / month), secure instant messaging and presence with Office Communications Online (at $2.50 / user / month), and Web conferencing with Office Live Meeting, a pre-existing service (now at $4.50 / user / month).
In a very compelling alternative package, though, the company is rolling all four of these services into a single bundle called Business Productivity Online Standard Suite, for $15 per user per month. Package licensing deals are available for "midmarket" customers with between 25 and 499 users, and "enterprise" customers with 500 users and above.
Compare this against the way licensing works now. Microsoft offers Exchange Server 2007 Standard Edition for $699 up front, plus $67 for each Client Access License (CAL). So in small-quantity bundles, just the CAL could be paid for in under seven months' time, which would leave a seven-person business another seven months to break even on the up-front costs.
However, just last week, Microsoft rolled out four buildouts of Small Business Server 2008 and Essential Business Server 2008, which include Exchange Server. For the Standard Edition of SBS 2008 (which does not include SQL Server), a five-CAL package sells for $1,089, plus $77 for each additional user. SBS also includes Windows Server 2008, of course, as well as SharePoint Services 3.0, and additional extras such as Forefront Security.
Technically, Microsoft's Online hosted services do not require Windows Server. However, if your business uses networked systems and if you want to take full advantage of Exchange synchronization, you should probably have a domain controller, which means one copy of Windows Server 2008 Standard Edition. That will get you Active Directory Services (AD DS, and yes, the "D" is indeed repeated there). You could get hosted e-mail without Windows Server, in which case you'd be running Outlook 2007 through Windows XP or Vista, but most of the ActiveSync functionality that Exchange provides would be useless. The street price for Windows Server 2008 Standard is about $749, coming down a bit since the rollout of SBS and EBS 2008, and you may still need additional CALs.
Source:betanews.com/article/Microsofts_new_hosted_services_What_are_your_options/1226954182
Wednesday, November 26, 2008
Train Signal Releases New Microsoft Server 2008 Active Directory Training
The comprehensive Windows Server 2008 Active Directory training features more than 20 hours of video instruction on two DVDs. Multiple file formats, such as iPod Video, Mp3 Audio, .WMV and .AVI, are available to make the training even more convenient. And students can print out the instructor's notes to follow along more easily and enhance the learning process.
The training package also helps students prepare for the 70-640 Configuring Windows Server 2008 Active Directory exam. It covers everything they need to know to pass the exam and includes the award-winning 70-640 practice exam software from Transcender, the world's leading exam simulation provider.
"This training package is perfect for anyone who wants to gain hands-on experience on Microsoft Server Active Directory 2008 and prepare for the 70-640 MCITP exam," said Iman Jalali, Train Signal's Director of Sales and Marketing. "We are pleased to offer this extensive package of training materials to help everyone from beginners to experienced administrators enhance their skills."
Train Signal's Windows Server 2008 Active Directory training package is designed to help students develop real skills that they can apply immediately. Key topics covered in the training include:
- Creating Domain Controllers
- User Account Creation
- Group Policy
- Back Up and Restore/Disaster Recovery
- Read-Only Domain Controllers in Server Core
- Sharing Folders and Files
- Remote Software Installation through Group Policy
- MCITP: 70-640 Certification
Source: marketwatch.com
Thursday, November 20, 2008
How to Schedule Active Directory Snapshots in Windows Server 2008
Microsoft recommends that you schedule regular snapshots, as this provides you with a quick method of checking the contents of the directory at different time slices in the past. One advantage of this that you can quickly identify which backup to use when needing to authoritatively restore accidentally deleted AD objects from backup.
Windows Server 2008 comes with a re-vamped Task Scheduler. You can configure tasks using both the UI as well as the command line (schtasks.exe). I prefer to use the command line as it has the advantage of allowing you to set tasks to run under the SYSTEM account. It is also the only option if you are using Server Core, unless you want to open the firewall to allow remote task scheduling from a computer running the full version.
Here’s the command line I use. Note that this is all on one line (wrapped here to fit page width).
SCHTASKS /Create /RU SYSTEM /SC DAILY /TN MYTASKS\DS_SNAPSHOT /TR “%windir%\system32\ntdsutil.exe sn \”ac i ntds\” create q q” /ST 05:00
It is worth pulling the command arguments apart to explain them better
/Create - pretty obvious. It instructs schtasks to create a new task.
/RU SYSTEM - the task will run under the SYSTEM account. Note that you don’t need to specify a password when using SYSTEM.
/SC DAILY- the task will run daily
/TN MYTASKS\DS_SNAPSHOT - I’ve called the task name DS_SNAPSHOT and this will be created within the MYTASKS task folder. The folder will be created automatically if it does not already exist.
/TR “%windir%\system32\ntdsutil.exe sn \”ac i ntds\” create q q” - This is the task action. It runs NTDSUTIL with arguments. Note that the double quotation marks within the arguments have to be escaped with the backslash character
/ST 05:00 - the start time for the task will be 5am.
The command line shown above assumes that you are working on the local machine on which you want to create the task. If defining the task for a remote computer, use the additional command line options shown below.
SCHTASKS /Create /S MYSERVER /U administrator /P xxxxx /RU SYSTEM /SC DAILY /TN MYTASKS\DS_SNAPSHOT /TR “%windir%\system32\ntdsutil.exe sn \”ac i ntds\” create q q” /ST 05:00
Once you’ve run the command you can verify the settings in the Task Scheduler UI.
Source:open-a-socket.com/index.php/2008/11/20/how-to-schedule-active-directory-snapshots-in-windows-server-2008/
See Also this :-
Restarting Active Directory as a service in Windows Server 2008
Wednesday, November 12, 2008
Active Directory-based soln for UNIX & Linux
DirectAuthorize centrally manages and enforces role-based entitlements for fine-grained control of user access and privileges on UNIX and Linux systems. This can eliminate a user's need to use the root account or other privileged accounts, thereby allowing those accounts to be securely locked down.
DirectAuthorize is the industry's first Active Directory-based solution for UNIX and Linux privilege management and delegation of root access. Leveraging a common architecture, DirectAuthorize is seamlessly integrated with Centrify DirectControl and complements DirectControl's comprehensive Active Directory-based authentication, access control and group policy support for non-Microsoft systems and applications.
"Unlike Windows Active Directory, UNIX lacks a simple and scalable model for administrative delegation," observed Ant Allan and Jay Heiser, Research Vice Presidents in the Gartner publication, Controlling UNIX Superuser privileges is Critical. "Organizations that allow root logins to mission- critical UNIX servers run unnecessary risks."
DirectAuthorize meets compliance-driven requirements for "least access" management by allowing organizations to centrally define logical roles (e.g. backup operator, DBA, web developer, application administrator, etc.) that carry with them the specific rights needed to perform duties within a role. DirectAuthorize's role-based architecture enables the following benefits:
- Simplify the execution of privileged commands --- users no longer need to switch to root or other privileged accounts
- Grant users rights to execute commands with elevated privileges, eliminating the need for access to privileged accounts and passwords
- Assign users a Restricted Environment with access only to a specific "whitelist" of commands
- Lockdown sensitive systems with fine-grained access controls that specify who can access a system and how
- Model date- and time-based access windows to match user roles
Like Centrify DirectControl, DirectAuthorize is tightly integrated into Active Directory, meaning no additional servers or infrastructure is required to run DirectAuthorize. DirectAuthorize stores its role and rights data securely in Active Directory Authorization Manager's existing rights-based logical model and data storage schema found in Windows 2003 and above.
This means no Active Directory schema extensions are required to install and use DirectAuthorize, and customers can leverage the pre-existing Authorization Manager (AzMan) tools and APIs to access DirectAuthorize's roles and rights data. DirectAuthorize is built on top of the DirectControl architecture, meaning the DirectAuthorize user interface is integrated with the DirectControl Administrator's Console and the DirectAuthorize rights enforcers are integrated into the DirectControl Agent. And unlike other solutions, DirectAuthorize requires no UNIX kernel changes or system reboots.
Via:ciol.com
Thursday, November 6, 2008
Macs to gain smart card-based login to Active Directory
On Wednesday, Centrify announced the release of its DirectControl 4.2 for Mac OS X software as well as the card client software supports Common Access Cards (CAC) and Personal Identity Verification (PIV) cards as well as with other cards that support the Apple TokenD interface. Dubbed Centrify DirectControl for Mac OS X Smart Card edition, the software will cost $90 for a single copy.
DirectControl 4.2 will come with some new security policies, the company said.
Finder Lock is one of more than 200 Mac-specific Group Policies that Centrify has developed to help administer Macs from the same centralized administrative tools from which Windows computers are managed. Other policies added in this release include enforcement of a computer policy to require smart card login, a removal policy to either lock the screen or force a logout when the smart card is removed, and additional security controls.
Improved support for Active Directory policies is one of the Mac headaches for IT managers in the enterprise. Smart card login will improve user experience.
For example, longtime Mac connectivity vendor Group Logic (the maker of Mass Transit) last month released the results of a survey of 350 IT pros about Mac/Windows IT issues. Some 70 percent of the respondents said they currently had Macs in their companies and an additional 6 percent were planning to bring in Macs in the “near term.”
Here was the hot list of Mac integration issues from the survey:
- Adapting Active Directory policy to support Macs — 38 percent.
- Help desk calls from Mac users — 35 percent.
- Compatibility and/or data corruption issues — 27 percent.
- Lack of IT/file naming policy enforcement tools — 25 percent.
- Maintaining the full “Mac Experience” for their end-users — 24 percent.
Tuesday, October 14, 2008
How To Use Ntdsutil to Manage Active Directory Files from the Command Line in Windows Server 2003
Windows Server 2003 Directory Service opens its files in exclusive mode. This means that the files cannot be managed while the server is operating as a domain controller.
To start the server in Directory Services Restore mode, follow these steps:
1. Restart the computer.
2. After the BIOS information is displayed, press F8.
3. Use the DOWN ARROW to select Directory Services Restore Mode(Windows Server 2003 domain controllers only), and then press ENTER.
4. Use the UP and DOWN ARROWS to select the Windows Server 2003 operating system, and then press ENTER.
5. Log on with your administrative account and password.
How to Install Support Tools and Start Ntdsutil
To install Windows Support Tools, follow these steps:
1. Insert the Windows Server 2003 installation CD in the CD-ROM or DVD-ROM drive.
2. Click Start, click Run, type drive_letter:\Support\Tools\suptools.msi, and then press ENTER.
To start Ntdsutil, click Start, click Run, type ntdsutil in the Open box, and then press ENTER.
NOTE: To access the list of available commands, type ?, and then press ENTER.
How to Move the Database
You can move the Ntds.dit data file to a new folder. If you do so, the registry is updated so that active directory service uses the new location when you restart the server.
To move the data file to another folder, follow these steps:
1. Click Start, click Run, type ntdsutil in the Open box, and then press ENTER.
2. At the Ntdsutil command prompt, type files, and then press ENTER.
3. At the file maintenance command prompt, type move DB to new location (where new location is an existing folder that you have created for this purpose), and then press ENTER.
4. To quit Ntdsutil, type quit, and then press ENTER.
5. Restart the computer.
How to Move Log Files
Use the move logs to command to move the directory service log files to another folder. For the new settings to take effect, restart the computer after you move the log files.
To move the log files, follow these steps:
1. Click Start, click Run, type ntdsutil in the Open box, and then press ENTER.
2. At the Ntdsutil command prompt, type files, and then press ENTER.
3. At the file maintenance command prompt, type move logs to new location (where new location is an existing folder that you have created for this purpose), and then press ENTER.
4. Type quit, and then press ENTER.
5. Restart the computer.
How to Recover the Database
To recover the database, follow these steps:
1. Click Start, click Run, type ntdsutil in the Open box, and then press ENTER.
2. At the Ntdsutil command prompt, type files, and then press ENTER.
3. At the file maintenance command prompt, type recover, and then press ENTER.
4. Type quit, and then press ENTER.
5. Restart the computer.
NOTE: You can also use Esentutl.exe to perform database recovery when the procedure described earlier in this article fails (for example, the procedure may fail when the database is inconsistent). To use Esentutl.exe to perform database recovery, follow these steps:
1. Click Start, click Run, type cmd in the Open box, and then press ENTER.
2. Type esentutl /r path\ntds.dit, and then press ENTER. path refers to the current location of the Ntds.dit file.
3. Delete the database log files (.log) from the WINDOWS\Ntds folder.
4. Restart the computer.
For additional information about the esentutl.exe utility, at the command prompt, type esentutl /?, and then press ENTER.
NOTE: This procedure involves transaction logs to recover data. Transaction logs are used to make sure that committed transactions are not lost if your computer fails or if it experiences unexpected power loss. Transaction data is written first to a log file, and then it is written to the data file. After you restart the computer after it fails, you can rerun the log to reproduce the transactions that were committed but that were not recorded to the data file.
How to Set Paths
You can use the set path command to set the path for the following items:
• Backup: Use this parameter with the set path command to set the disk-to-disk backup target to the folder that is specified by the location variable. You can configure Directory Service to perform an online disk-to-disk backup at scheduled intervals.
• Database: Use this parameter with the set path command to update the part of the registry that identifies the location and file name of the data file. Use this command only to rebuild a domain controller that has lost its data file and that is not being restored by means of typical restoration procedures.
• Logs: Use this parameter with the set path command to update the part of the registry that identifies the location of the log files. Use this command only if you are rebuilding a domain controller that has lost its log files and is not being restored by means of typical restoration procedures.
• Working Directory: Use this parameter with the set path command to set the part of the registry that identifies Directory Service's working folder to the folder that is specified by the location variable.
To run the set path command, follow these steps:
1. Click Start, click Run, type ntdsutil in the Open box, and then press ENTER.
2. At the Ntdsutil command prompt, type files, and then press ENTER.
3. At the file maintenance command prompt, type set path object location, and then press ENTER. object refers to one of the following items:
• Backup
• Database
• Logs
• Working Directory
location refers to the location (folder) to which you want to set the object identified in the command.
4. Type quit, and then press ENTER.
Source: support.microsoft.com/kb/816120
Thursday, August 7, 2008
What is Active directory
An active directory (sometimes referred to as an AD) does a variety of functions including the ability to provide information on objects, helps organize these objects for easy retrieval and access, allows access by end users and administrators and allows the administrator to set security up for the directory.
An active directory can be defined as a hierarchical structure and this structure is usually broken up into three main categories, the resources which might include hardware such as printers, services for end users such as web email servers and objects which are the main functions of the domain and network.
It is interesting to note the framework for the objects. Remember that an object can be a piece of hardware such as a printer, end user or security settings set by the administrator. These objects can hold other objects within their file structure. All objects have an ID, usually an object name (folder name). In addition to these objects being able to hold other objects, every object has its own attributes which allows it to be characterized by the information which it contains. Most IT professionals call these setting or characterizations schemas.
Depending on the type of schema created for a folder, will ultimately determine how these objects are used. For instance, some objects with certain schemas can not be deleted, they can only be deactivated. Others types of schemas with certain attributes can be deleted entirely. For instance, a user object can be deleted, but the administrator object can not be deleted.
When understanding active directories, it is important to know the framework that objects can be viewed at. In fact, an active directory can be viewed at either one of three levels, these levels are called forests, trees or domains. The highest structure is called the forest because you can see all objects included within the active directory.
Within the Forest structure are trees, these structures usually hold one or more domains, going further down the structure of an active directory are single domains. To put the forest, trees and domains into perspective, consider the following example.
A large organization has many dozens of users and processes. The forest might be the entire network of end users and specific computers at a set location. Within this forest directory are now trees that hold information on specific objects such as domain controllers, program data, system, etc. Within these objects are even more objects which can then be controlled and categorized.
Monday, July 14, 2008
Active Directory management
Their manager calls the help desk, which calls IT support to action the changes in AD. Once these are made, the manager is notified that the user has been set up. This can take hours, sometimes days. Not only does this process tie up IT with mundane admin chores, but it can mean that staff can't be productive during this hiatus. The other side of the coin applies equally - you can't remove a user's access rights immediately.
Active Directory offers a cost-effective solution. It neatly overcomes these AD admin headaches by effectively delegating AD object management to line managers. If changes have to be made, managers can make them on the spot, with changes going live in as little as ten seconds.
Active Directory uses a web-based AD management interface - it can be installed quickly through a company's internal network as there are no desktop clients to install, and the familiar web-browser user interface cuts the need for training. In fact, it's so simple and intuitive that most staff probably won't need any training.
Active Directory provides granular access control to entrusted staff with no limitations. Once logged in your presented with a home page offering just three options: update access, view access groups and view audited history. Changes to the AD are made via a wizard. A search option is provided, useful if you have thousands of AD objects to contend with.
When you have finished making your changes you simply click the "update all groups" button and it's done.
Paperwork is kept to a minimum. Changes to working practices and user privileges are managed through work flow emails. As well as greatly simplifying AD admin for both line managers and IT support staff, security is also improved by automating a usually manual security process. All Active Directory updates are logged to allow for auditing, which is essential to meet compliance standards.
In fact, Active Directory management can be standardized worldwide and can be used as part of the enterprise's Quality Management. The audit history option on the home page lets you view log information by group/role, date or user. Data can be downloaded and displayed in Excel.
Although Active Directory is a standalone product and doesn't integrate with other network management tools, its web services programming interface (API) will allow the integration of separate systems. As a result, Active Directory can complement existing identity management or account provisioning solutions. At the moment, Active Directory can support up to 100,000 users. System pre-requisites include Windows Server 2000/2003, IIS 6,.NET Framework 1.1, an SMTP e-mail server and MS SL Server, either 2000, 2005 or Express 2005 - most organizations contemplating deploying Active Directory will most likely meet these criteria from the off.
Installation is a doddle - in fact, if you spend more than ten minutes on it, you're probably doing something wrong.
In conclusion, Active Directory is an AD management tool that's well-suited to organizations with more than 300 seats, as well as to managed-data centers looking for a painless and secure method of passing security management tasks back to the client.
Source:securecomputing.net
Tuesday, July 8, 2008
Windows Server 2008
Over the weekend I installed the released version of Windows Server 2008 (after having worked with the release candidate previously), and the experience reminded how impressed I am by Win2008's ease of installation. I have a Intel quad-CPU set up, along with some 7200rpm drives because I do a lot of testing, and the 64-bit version Windows Server 2008 Standard Edition installation just flew onto my hard drive. Following that, deciding what you want your Win2008 to be in life is a relatively straightforward, guided process.
If you are new to Win2008, it includes something called Server Roles. What do you want this server to be? An Active Directory domain controller (called Domain Services), a file or print server, an IIS Web server, a combination, or maybe something else? Win2008 comes with some 17 Server Roles, each comprising a number of appropriate options. Let's say you want to set up a multipurpose server as a domain controller, DHCP server, file server, print server and Web server -- a configuration you might use in a smaller organization. Each of those functions are Server Roles within Win2008. Active Directory Domain Services will also require you set up the server using the DNS Server role.
Each Server Role starts with a wizard for basic configuration information (like setting up scopes for the DHCP Server role, for example) and concludes with an installation step. If some feature selections within a Server Role have other software dependencies, those are shown with an easy-to-understand "okay" box to add those to the installation. If you are a beginner or don't happen to know about a certain feature set within a Server Role, help is there right upfront about what it does and the installation options that may be relevant to you (like setting up a new domain vs. adding a controller to an existing domain services forest).
You'll likely have to reboot Win2008 after most installation steps, so you'll want to get everything installed and configured before a bunch of users sign on. While there's a big difference in pricing, I've found Win2008 Standard Edition about as easy to set up as the Win2008 Small Business Edition. SBE obviously consolidates some steps, but Win2008 isn't all that hard to set up -- the basic stuff anyway. If you are going to exceed the license restrictions, don't fear setting up Win2008, as it's not that much harder.
Tuesday, July 1, 2008
Active Server Directory
An active directory (sometimes referred to as an AD) does a variety of functions including the ability to provide information on objects, helps organize these objects for easy retrieval and access, allows access by end users and administrators and allows the administrator to set security up for the directory.
An active directory can be defined as a hierarchical structure and this structure is usually broken up into three main categories, the resources which might include hardware such as printers, services for end users such as web email servers and objects which are the main functions of the domain and network.
It is interesting to note the framework for the objects. Remember that an object can be a piece of hardware such as a printer, end user or security settings set by the administrator. These objects can hold other objects within their file structure. All objects have an ID, usually an object name (folder name). In addition to these objects being able to hold other objects, every object has its own attributes which allows it to be characterized by the information which it contains. Most IT professionals call these setting or characterizations schema's.
Depending on the type of schema created for a folder, will ultimately determine how these objects are used. For instance, some objects with certain schema's can not be deleted, they can only be deactivated. Others types of schema's with certain attributes can be deleted entirely. For instance, a user object can be deleted, but the administrator object can not be deleted.
When understanding active directories, it is important to know the framework that objects can be viewed at. In fact, an active directory can be viewed at either one of three levels, these levels are called forests, trees or domains. The highest structure is called the forest because you can see all objects included within the active directory.
Within the Forest structure are trees, these structures usually hold one or more domains, going further down the structure of an active directory are single domains. To put the forest, trees and domains into perspective, consider the following example.
A large organization has many dozens of users and processes. The forest might be the entire network of end users and specific computers at a set location. Within this forest directory are now trees that hold information on specific objects such as domain controllers, program data, system, etc. Within these objects are even more objects which can then be controlled and categorized.



