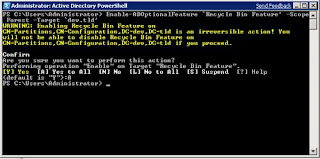
Once this is complete, you can view the contents of the Active Directory Recycle Bin. This special location exists as a container that holds the objects as they are deleted.
In my first looks at Windows Server 2008 R2 beta, I set up a test domain running at that function level. The domain, dev.tld, had nothing in the Recycle Bin after it was created. I deleted two objects: one user and one group. Figure B shows the query of what is in the Recycle Bin before the two objects were deleted, then another query after they were deleted.
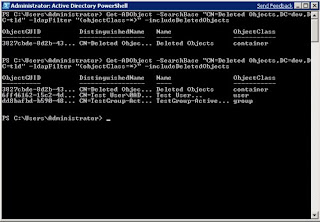
Notice that some fields were cut off in the display, notably the full GUID (which is needed for the restore). To display the entire GUID and object name, you would run this query:
Get-ADObject -SearchBase "CN=Deleted Objects,DC=dev,DC=tld" -ldapFilter "(objectClass=*)" -includeDeletedObjects | FT ObjectGUID,Name -A
Then, the full GUID is displayed, so a copy and paste operation will allow an easy restore. From the list above, to restore the single user named test, the following command will perform the restore:
Restore-ADObject -Identity 6ff46162-15c2-4d42-8e15-2fcac5c8422e
The object is instantly returned to full existence in Active Directory.
Source: http://blogs.techrepublic.com.com/datacenter/?p=675



